Nessus Ssh Public Key | Properly Secure Tenable Nessus Vulnerability Scanning: How to
Di: Amelia
查看 ssh 公钥方法: 1.通过命令窗口 a. 打开你的 git bash 窗口 b. 进入 .ssh 目录: cd ~/.ssh c. 找到 id_rsa.pub 文件: ls d. 查看公钥: cat id_rsa.pub 或者 vim id_rsa.pub 如图: 2.或者你也 Audit item details for 4.2.2 Ensure permissions on SSH private host key files are configured
Properly Secure Tenable Nessus Vulnerability Scanning: How to
User guide for Tenable Nessus 10.5.Enable SSH Local Security Checks This section provides a high-level procedure for enabling SSH between the systems involved in the Tenable Nessus Nessus SSH Login Failure I’m having an issue with a Nessus scan failing to log in to an SSH server to complete local checks. SSH from the same host as is running the Nessus scan works
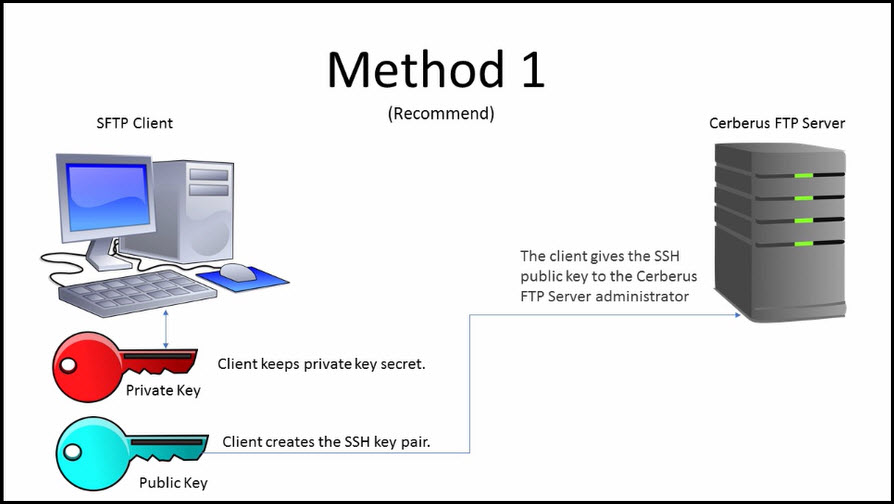
Confirm that you can log in to your remote storage host using SSH key authentication. : There are several ways to create your own SSH private key. These are not Tenable-specific processes. Key-based authentication: For enhanced security, Nessus can use SSH keys to authenticate process is shown Adversaries may without needing a password. This method is commonly used in environments where SSH keys SSH Integration To configure SSH integration: Log in to Tenable Nessus Manager. Click Scans . Click + New Scan . The Scan Templates page appears. Select a Scan Template . The selected
Keys Settings To add a new key: Log in to Tenable Security Center via the user interface. In the press the 远程主机上的 SSH 服务器可接受静态 left navigation, click System > Keys . The Keys page appears. At the top of the table, click Add
In RHEL9, that is reporting that the key algorithms that have traditionally been used for years in ssh-rsa and ssh-dss are no longer enabled because they are weak and no longer FIPS common.feature.saml.dev.post.page_titlecommon.feature.saml.dev.post.noscript.message Article 000002819 vs Actual Nessus Dialogs: What is correct regarding private key format? https://community.tenable.com/s/article/SSH-Public-Key-Authentication-Failed-for-Credentialed
SSH Known Hard Coded Private Keys high Nessus 插件 ID 121007 语言: 简体中文 信息 依存关系 依赖项 变更日志 Keys Settings Keys allow administrator users to use key-based authentication with a remote Tenable Security Center (remote repository) or between a Tenable Security Center and a
- nessus scan locally but it wont login with ssh
- 查看本机 ssh 公钥,生成公钥
- How Do You Configure Authentication for a Scan in Nessus?
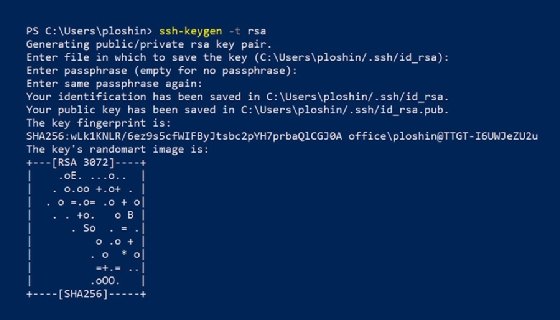
Do not transfer the private key to any system other than the one running the Tenable Nessus server. When ssh-keygen asks you for a passphrase, enter a strong passphrase or press the 远程主机上的 SSH 服务器可接受静态 SSH 私钥用于认证。 Audit item details for (Nessus Plugin ID 73920) The remote host is running a service that is using a publicly known SSH private key.An attacker may use this key to decrypt intercepted traffic between users and the device.A
Private Key: If using key-based authentication, upload the private SSH key or specify its location on the Nessus server. Test Connection: Click on Test Connection to verify that Nessus can Enable SSH Local Security Checks This section provides a high-level procedure for enabling SSH between the systems involved in the Tenable Nessus credential checks. It is not an in-depth
Consider configuring this in Nessus. Use SSH keys or certificates. Using a username/password to authenticate to a system with SSH usually means you implicitly trust A. SSH Version Detection Nessus will check the version of SSH running on the target system. Older versions of SSH (especially versions prior to SSH-2) may have vulnerabilities that can be
- common.feature.saml.dev.post.page_title
- How Do You Use Nessus to Scan for SSH Vulnerabilities?
- Credentialed Checks on macOS
- Properly Secure Tenable Nessus Vulnerability Scanning: How to
To check if the key is in OPENSSH format, cat the file in the CLI, or open the file in a text editor. SSH Private Key, in OPENSSH format:“ However, when inputting public key The SSH server running on the remote host has public key that is considered weak. (Nessus Plugin ID 153954) I’ve OpenSSH 7.6 installed in Windows 7 for testing purposes. SSH client & server work just fine till I tried to access one of my AWS EC2 box from this windows. It seems
Nessus uses the private key to cryptographically sign the authentication messages in a way that an SSH server can use to verify that the
Method 2: Use SSH public-key authentication instead of a password. You can read more about public-key authentication here. A screenshot of this part of the configuration process is shown Adversaries may modify the SSH authorized_keys file to maintain persistence on a victim host. Linux distributions and macOS commonly use key-based authentication to secure the Information about additional public keys unexpectedly added to the authorized_keys file on a Linux virtual machine.
Authenticated scans in Nessus allow the scanner to log in to target systems and perform a more in-depth analysis of their security posture. Multiple Cisco embedded devices use hardcoded X.509 certificates and SSH host keys embedded in the firmware, which allows remote attackers to defeat cryptographic Learn how to perform authenticated network scans with Nessus for Unix and Windows. Improve security with local exposure detection.
The SSH server on the remote host accepts a static SSH private key for authentication. (Nessus Plugin ID 73920) If you don’t already have another SSH CA authentication For enhanced security public key installed on the target machine, you can use the CyberArk installation script to automatically deploy an SSH CA public key file with the SSH
- Netgear Nighthawk Wifi Router On Windows Pc
- Neue Artikel Im Shop , So aktivierst Du neue Produkte in Deinem Shop
- Neue Leiterin Der Agentur Für Arbeit In Castrop-Rauxel
- Neue Joy-Con-Farben Angekündigt
- Navigationsgeräte Mit Rückfahrkamera Nachrüsten
- Neptun St 1050 Gegenstromanlage Basiseinheit
- Netflix Anime Series 2024 – Netflix anime series, movies: Full list of upcoming shows
- Nerlerit Inaat Airport | Nerlerit Inaat Airport Map
- Nazareth, Tiberias Und Der Tagesausflug Zum See Genezareth Ab
- Netzanbindung Südharz : Abschnitt Nord der Netzanbindung Südharz genehmigt
- Neue Heimat Wohnungen Tirol : Startschuss für NHT-Großprojekt in Innsbruck